I recently set up a new server for a project, and when I looked at the access logs, I was surprised to see it was already being actively scanned for exploits.
And these were site-specific logs, meaning it wasn't just the server's IP address getting scanned, but the host name for this new staging domain I just set up.
How could this be? How would an attacker know about this new domain that I just created?
There's an interesting clue in the logs. Take a look and see if you can spot it:
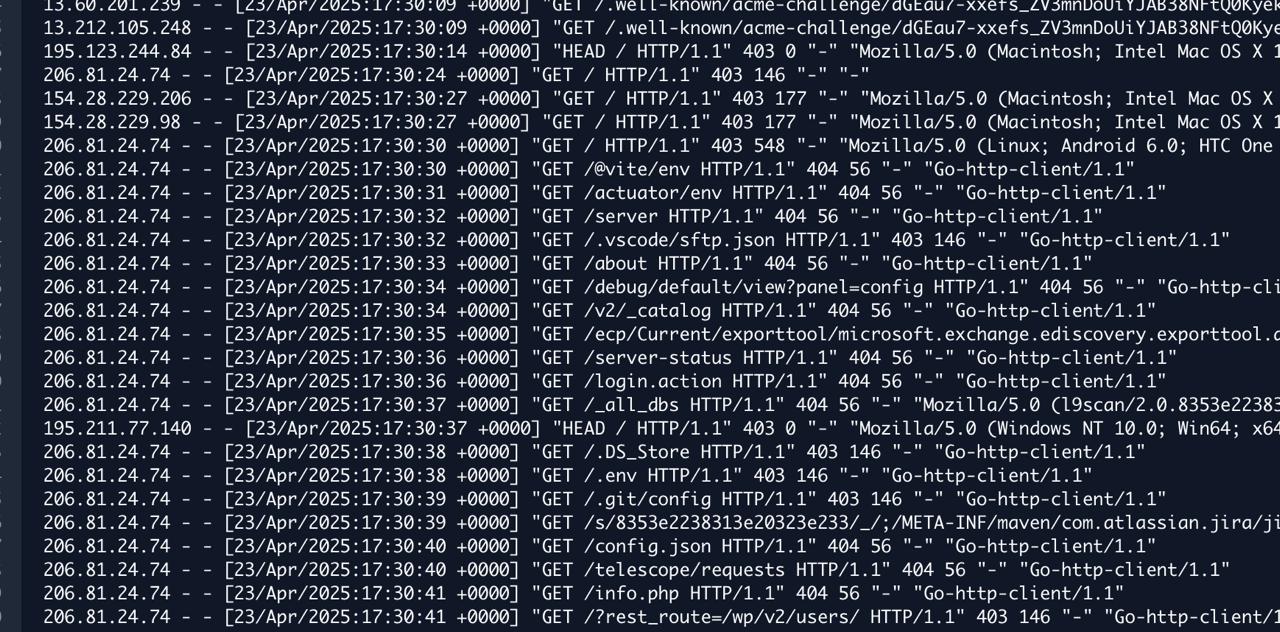
Notice that the very first two log entries mention acme-challenge.
These two requests are challenges required for the issuance of a TLS certificate using Let's Encrypt.
Five seconds after the certificate was issued, the flood of probe requests began. What is the connection?
Certificate authorities, like Let's Encrypt, publish a list of newly-issued certificates in a public database called the Certificate Transparency log. This allows a domain owner to monitor for unauthorized issuance of certificates for their domain.
However, this also means that attackers can monitor this log to find domains they want to target, even domains used for "secret" staging environments with brand-new servers.
So never assume that no one will find your server just because it's new or not yet publicized. Always take the necessary precautions to secure your server from the start.
Here to help,
Joel
P.S. Security is an important consideration when building your Laravel app. Download our free book: 7 Steps to a Secure Laravel App.

